Securing Your Computer
September 22, 2004Overview
This help document is primarily written for users of Microsoft® Windows®, although the ideas here apply to all computer users. The focus here is to provide basic precautions that should be taken by every user to avoid being infected by a computer virus. In addition to protecting yourself against viruses, by following these guidelines you will also go a long way to securing your computer against most types of hacker attacks as well.
What is a computer virus? A virus is any program that is installed on your computer system without your knowledge or consent. Sometimes viruses can spread by themselves. Other times they require some human intervention, usually by tricking you into running them. Sometimes they are called 'worms' or 'trojan horses', depending on the method of attack or means of spreading. For simplicity's sake, we will refer to them all as 'viruses.' Most viruses negatively affect the computer they are running on, although not always in a way that is noticeable to you, the end-user.
These malicious programs spread not only through email, but through web pages, chat and instant messaging services, local area network file sharing, CDROM and floppy disks, and more. Any software that connects you with other computers in any way is a risk for infection.
Tip: Microsoft offers free virus-related phone support: 1-866-PCSAFETY
We will start out with the things that all users should do, then we will provide some things that you should do based on which brand of programs you use for the Internet. We can't cover everything, but we will go over the most popular programs.
- Your computer could be infected with a virus right now...
- Use Anti-Virus Software, and Keep It Updated
- Secure Your Internet Connection With a "Firewall"
- Keep Windows Updated
- Keep Internet Programs Updated
- Program-Specific Security Tips
- Turn "File Sharing" Off
- Beware Forged Emails & Phishing Scams
- Practice Safe Computing
- Conclusion
- For More Information
Your computer could be infected with a virus right now...
... and you might not even realize it. In fact, if you are on a high-speed internet connection, and you don't have at least a software firewall installed, you are likely already infected with at least one type of virus, worm, or trojan horse!
Most viruses are spread by people who don't realize they are infected. But if they aren't affecting your computer enough for you to notice them, why should you care that you're infected?
Viruses can destroy your important data, expose passwords and credit card numbers, reveal personal, private information and email correspondence, help criminals attack internet websites, send spam to all your contacts, and more, all without your knowledge. Viruses can provide "open back doors" that even novice hackers can then use to easily enter your system.
Once a hacker has access to your system, they cannot only steal your private data, but also use your infected computer to attack or hack into other computers, leaving you with the blame and responsibility for the damage caused. Most people that are infected don't even realize it. The most successful viruses don't make themselves known to you until it's too late: you could have a hidden virus using your computer to send infected email or instant messages to your friends and family right now -- messages that appear to come from you, or messages forged to look like they are coming from someone you've made contact with a long time ago. Your computer could be being used in an attack on another computer or network right now, and in most cases, you would not even realize it.
It is your moral and legal responsibility to make sure you keep your computer secure and virus free at all times. It protects you and everyone else on the Internet.
Securing your computer is not difficult, and there are a few, easy
"safe computing" habits that will prevent most viruses and
other security breaches. Please read this entire document to help
you secure your computer. We hope this will help you practice Safe
Computing at all times!
Use Anti-Virus Software, and Keep It Updated
The first thing you need to do is obtain and install anti-virus (A/V) software, and completely scan all computers on your local network for viruses, as soon as possible. Here is a Google web search that will give you a list of several A/V software products to choose from. We frequently recommend Norton AntiVirus, but there are many good programs available. TrendMicro even offers a free online virus scan that can at least detect if you're infected with a virus (although we recommend obtaining a complete, standalone A/V software program).
Most A/V software, such as Norton AntiVirus, will scan your entire computer system, any files you download from the internet, any files sent from instant messaging programs, and any files that you receive via email.
After you install the A/V software, you should run its update utility to get the latest virus "signatures" before doing a full system scan. Virus signatures are like fingerprints that are used to identify viruses embedded in files on your computer. Without the latest signatures, your A/V software will overlook new viruses! Most of the A/V companies provide subscription services to keep your virus software up-to-date.
Once your system is found to be clean, setup your A/V software to run a weekly virus scan, and to notify you (at least) once a week to update the virus signatures, or do it automatically if that's an option. New viruses are discovered DAILY, so this is an important step.
Next, if your software offers this feature, turn on "email virus scanning." This should scan all your incoming (and possible outgoing) email for virus attachments. If it finds a virus, it will prevent you from being able to accidentally run it, usually by deleting or renaming the file.
Remember, it is CRUCIAL that you keep your A/V software updated, and regularly scan your system!
Secure Your Internet Connection With a "Firewall"
If you are running Windows, most likely you have a lot of network ports that are currently open. These ports allow incoming and outgoing communication, and unfortunately, they are prone to attack via the Internet. Some of these ports can even reveal private information to outside attackers. In most cases, none of these ports need to be available from the Internet. What you need to protect yourself is a "firewall." Like it's name implies, a firewall is a barrier. This barrier tries to prevent most traffic from entering (or leaving) your home computer network.
Sadly, if you aren't using any type of firewall now, your computer is absolutely wide open to hundreds of well-known attacks and viruses that are active on the Internet right now. In fact, chances are very good that if you are on a high-speed connection right now without a firewall, your system is already infected with at least one virus, worm or trojan horse. This is why we recommend putting a firewall in place before ever connecting your machine to the Internet.
For $75 or less, you can purchase an adequate hardware firewall that can protect every computer in your house or office from the most common attacks. The key is to get it in place BEFORE you connect to the internet for the FIRST TIME, otherwise it is too late. This is especially true if you are connecting a machine with a fresh installation of Windows, because you haven't been able to update the known security flaws before an automated attack can exploit them. We have seen machines infected within 6 minutes of connecting them to the Internet.
Install a firewall before you connect to the Internet for the first time! If you're already infected, disconnect from the Internet (after installing the tools necessary to clean your machine(s) infections), clean the infections, install a firewall, and then re-connect to the Internet.
Hardware Firewalls
You should strongly consider purchasing a "hardware firewall." These is an appliance that sits between your internet connection (such as a cable or DSL modem) and your computer. Often times it will be combined with a switch or router so that multiple computers can be connected to your internet connection securely. A hardware firewall typically blocks all incoming traffic (from the internet to your computers), and allows all outgoing traffic (from your computers to the internet). You can probably find a Linksys router with a firewall included at your local computer store for $75 or less.
The advantages to using a hardware firewall are that they can protect your entire network from one centralized location, they are typically harder to bypass than software firewalls, they offer some features not available from the software firewalls (such as Network Address Translation), and most importantly they can protect your machines from attack when you first put a machine on the internet and are trying to update the operating system with the latest patches. Some hardware firewalls can even provide virus scanning for your entire network's incoming traffic.
This Google search is a list of dedicated firewall appliances that are available. These are generally more expensive, but offer more features than those found in the Linksys routers. However, even the inexpensive Linksys router would be preferred to the Software Firewalls if you have to choose between one or the other.
Software Firewalls
Software firewalls are the most common and least expensive. Although they cannot normally protect you completely when first connecting to the internet and updating your operating system and internet programs, they are definitely a start in the right direction. If you cannot find a hardware firewall, consider buying a program like Zone Alarm from your local computer store, and installing it before you connect your machine to the internet for the first time!
Currently, the software firewall we recommend the most often is ZoneAlarm (free for personal use), although there are many available. ZoneAlarm blocks access to the ports described above, preventing most hacker attacks. It also allows you to control which programs have access to the Internet -- each time a program wants to use the network, it asks you for permission. You can say Yes or No, and even tell it to remember your decision for the future. We highly recommend this if you are a novice computer user.
(Note that the 'firewall' which comes with Windows XP is generally considered not to be adequate for the job of protecting your PC from all attacks. We advise obtaining a third party product in addition, such as ZoneAlarm. It is rumored that Microsoft will be improving the built-in firewall in Service Pack 2, for Windows XP, available in Fall 2004.)
Keep Windows® Updated
Even if you have a firewall and anti-virus software, if you don't keep Windows patched with the latest fixes, you have a breach in your armor that can be exploited.
You should visit Microsoft's Windows Update site at least once a week to see if any new updates for Windows have been released. (You will need to visit that site in Internet Explorer.) Any new security flaws that have been fixed in Windows should be posted here for you to easily update Windows. If you don't do this, your system could be wide-open to the latest hacker threat.
Newer versions of Windows, like Windows 2000 and XP, have options available that you can turn on so that your computer will proactively monitor the Windows Update site for new patches. In newer versions of Windows, you can even have it install the patches for you, although you may want to exercise more control over mission-critical computers at work.
The location of these automatic update options varies depending on which version of Windows you are using, however you will need to start by opening Control Panel. Windows XP/2003 users should then run the "System" applet, and change to the "Automatic Updates" tab to find these options. Windows 2000 users should look for an "Automatic Updates" applet and run that.
Keep Internet Programs Updated
On a regular basis, you should check the homepages for your internet programs (web browser, email client, chat program, etc.), and make sure they are updated with the latest security patches and upgrades. Your computer is only as secure as the weakest link! As an example, a very widespread virus is able to open itself automatically using a flaw in Outlook Express which was fixed over a year ago -- yet if you haven't updated Internet Explorer, you are at serious risk of being infected.
Microsoft has a document you should read that focuses on security for home users. It's called "Three Steps to Help Ensure Your PC is Protected." Some of the information is the same as what you've read on this page, but they also provide many links to other information on their site for more details on certain points.
The most important thing to do is locate the homepages for the various internet programs you use, and bookmark them. Then visit them periodically to check for new updates on your software.
Program-Specific Security Tips
Here are some security tips for some of the more popular Internet programs in use today.
Microsoft Internet Explorer and ActiveX
SECURITY WARNING: Due to the regular, severe security problems with Internet Explorer, we highly recommend using a different web browser for your everyday browsing, and use Internet Explorer only for things like Windows Update. Consider trying a 3rd-party browser, such as Mozilla Firefox (web browser), Opera (web browser), or Mozilla Suite (a web, email, newsgroups, and IRC suite).
The iATN staff uses Firefox, as we've had a very positive experience overall with this browser. It has proven to be much more secure than Internet Explorer, in part due to it's separation from the operating system, as well as its foundation as an open source program with many active developers.
Please keep in mind: as with any software product, you must make sure to keep these alternate browsers up-to-date to stay secure.
Even if you don't use Internet Explorer normally, because it is embedded in Windows and used by many 3rd-party programs to display web content (such as AOL, Quicken, etc.), it is very important to keep IE updated, so that any known security problems can be fixed.
ActiveX is a part of MSIE which allows full Windows programs to run from inside your web browser. These programs, known as "ActiveX Controls," can do anything a normal program can do on your computer, so be careful. We recommend setting up MSIE so that it will prompt you to download signed ActiveX controls, and to not download unsigned controls at all. This allows you to decide when to run an ActiveX control from a company. Do not run ActiveX controls from untrusted or unknown sources, or you could wind up with a virus like this one.
We recommend the following settings for ActiveX in MSIE:
- Download signed ActiveX controls: PROMPT
- Download unsigned ActiveX controls: DISABLE
- Initialize and script ActiveX controls not marked as safe: PROMPT
- Run ActiveX controls: ENABLE*
- Script ActiveX controls marked safe for scripting: ENABLE
You can control these settings by going to the Tools menu, select Internet Options (or "Options" on some earlier versions of MSIE). Then select the Security tab, and press the "Custom Levels" button. Scroll down that list to find the settings above. The wording of the options may be slightly different.
Note: To be completely safe, you can disable ActiveX by setting option #4 above to DISABLE. However, many pages will annoy you with a popup window saying they can't be displayed properly, because the popular Macromedia Flash software is an ActiveX control.
Microsoft Outlook Express
SECURITY WARNING: Due to the regular, severe security problems with Outlook and Outlook Express, we highly recommend using a different email program. Consider trying a 3rd-party email program, such as Mozilla Thunderbird (web browser) or Mozilla Suite (a web, email, newsgroups, and IRC suite).
If you use Outlook Express (OE), and are not using version 6 (available in Internet Explorer 6), we highly recommend upgrading now. Once you have finished that, please come back here and continue securing OE.
Newer versions of OE offer some added protection against viruses. One setting causes HTML email to be opened in a restricted environment (preventing things like JavaScript from running in an email). Another setting makes OE prompt you if a program is trying to send email in the background using OE (a common virus exploit). And the third setting allows you to block access to executable attachments (this feature is available only in OE 6 and later).
To turn these features on, open OE and select the "Tools" menu. Then select the "Options..." menu item. Select the "Security" tab, and you should see these options in the Virus Protection area:
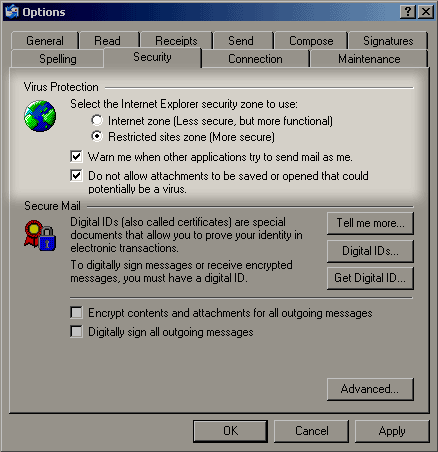
Microsoft Outlook
Outlook 2002 (XP) is the most secure version of Outlook, yet. By default, it will not allow you to access any executable attachments. If possible, we recommend upgrading to this version, or the latest version of Outlook (Office) available to you.
For Outlook 2000 and Outlook 98, there is a security patch available which implements the same security model as that in Outlook 2002/XP and later (no display of executable attachments). We highly recommend applying this security patch immediately if you can't upgrade to the latest release of Outlook (usually sold as part of the Microsoft Office suite).
In addition, you need to go into the "Tools" menu, select the "Options..." menu item, and then the "Security" tab. Make sure the "Zone" setting is set to "Restricted Sites," like this:
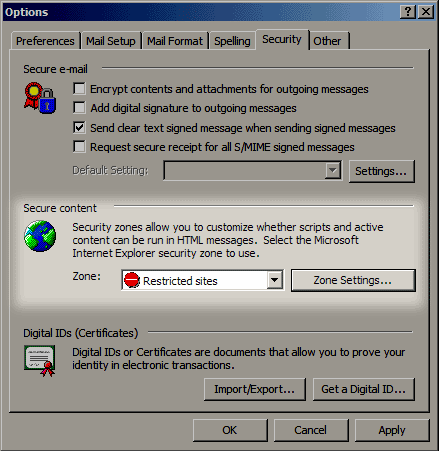
Instant Messaging and Chat Programs: AIM, Messenger, ICQ, mIRC, etc.
If you use instant messaging (I/M) programs, it is important to keep them up-to-date, and to keep an eye out for new security issues. Here are some helpful links for the most popular I/M and chat clients:
- Microsoft Messenger Homepage
- AOL Instant Messenger (AIM) Download Page / Security FAQ
- ICQ Download Page / Security Page / Virus Avoidance
- mIRC Download Page / Latest News
- Trillian Download
Page / Latest News
The important thing to remember is that it is possible for viruses to be sent through these instant messaging networks -- it's already been done. We recommend rejecting any file download attempt made by these programs, even if you know the sender (because it could be a virus forging itself as your buddy), unless you are expecting the attachment, it is NOT executable, and you have scanned it with your A/V software.
Microsoft Office
Even though this is not really an "internet program," the Microsoft Office suite uses a lot of internet-based technologies, and is therefore susceptible to virus and hacker attacks. We highly recommend keeping your Office programs up-to-date, by visiting Microsoft's Office Product Update center.
Netscape/Mozilla
While most exploits have been found in Microsoft internet products, there have been security problems in some versions of Netscape products. We advise you to upgrade to the latest version immediately.
If you enjoy Netscape Navigator/Communicator, we think you will be even more pleased with the newer versions based on Netscape's open source code. The mozilla project offers an excellent browser called Mozilla Firefox, as well as an email client that gives Outlook Express a run for its money, Mozilla Thunderbird. These programs have shown themselves to be far more secure than their Microsoft competitors. There is also a Mozilla Suite which combines the browser, email program, newsreader, and IRC chat client.
Netscape's email program does not offer a way to prevent access to executable attachments, like Outlook 2002 does, so you should exercise care with incoming attachments, and be sure to have your A/V software scan your incoming email. The only other thing to be careful about is to NOT enable JavaScript in mail & newsgroups. (It is off by default in Netscape 7 and Mozilla.) You can check this setting in Edit >> Preferences >> Advanced >> Scripts & Plugins. "Enable Plugins for Mail & Newsgroups" should also be turned off (it is by default).
Eudora
First, make sure you have the latest version installed. Next, go to Tools >> Options >> Viewing Mail and make sure "Allow Executables in HTML Content" is not on (it is OFF by default). Eudora does not offer a way to prevent access to executable attachments, like Outlook 2002 does, so you should exercise care with incoming attachments, and be sure to have your A/V software scan your incoming email.
Turn "File Sharing" Off
The most common way viruses spread is via email. However, that is not the only way. Viruses can also spread themselves using Windows file sharing. For example, let us say you and your kids both have a computer on your LAN, sharing the same internet connection. If file sharing is turned on, it could be possible for your kids' computer to be infected with a virus, which then spreads itself to your computer via file sharing. File sharing could also allow a hacker easier access to your files.
Unless you need to share files with someone on your LAN, you should turn file sharing OFF. Depending on which version of Windows you use, the procedure differs slightly.
In Windows 95/98/Me, you can turn it off by selecting Start >> Settings >> Control Panel. When Control Panel opens, double-click on "Network." You should see something similar to this:
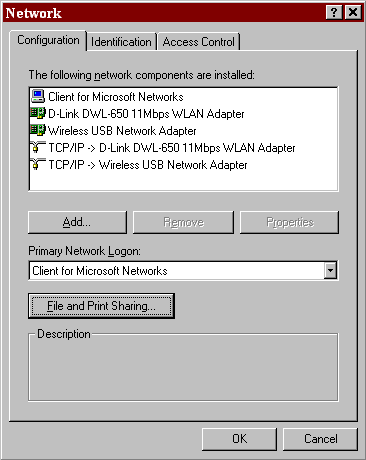
Now click on the "File and Print Sharing..." button (highlighted). You will see a screen like the one below, and you need to turn off the checkbox next to "I want to be able to give others access to my files" (highlighted below). You can also disable printer sharing if you don't need to share your printer, for added safety.
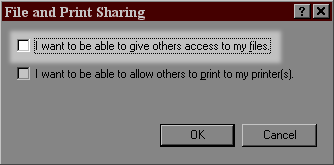
Once you press OK to close that dialog, and again for the Network window, file sharing should be sealed off from viruses and hackers.
In Windows XP, it's a little bit different. You need to go into Control Panel, open the Network Connections program, and double-click your primary internet connection. This will pop up a window similar to the one below:
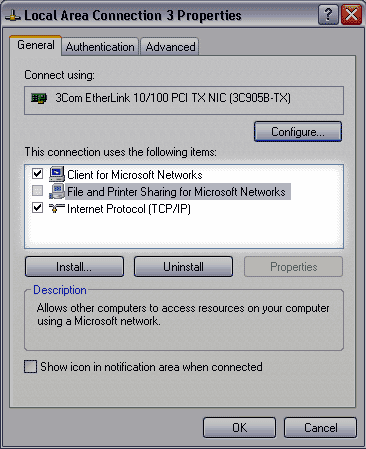
You want to turn off the check box next to "File and Printer Sharing for Microsoft Networks," (highlighted above) and then press OK. If you have network connections set up, you should perform this step for all of them, to be safe. Now your file sharing should be sealed off from viruses and hackers as well.
What If I Need to Share Files?
For those of you that need to be able to share files with other computers on your LAN, you will have to keep file sharing turned on. However, it is CRUCIAL that you at least make sure the files and folders you share are password protected. Windows allows you to share folders without specifying a password, but if you do this, it is very insecure, and a hacker could easily infiltrate your system. To turn on password protection, right-click on the folder you are sharing, and look for a menu option to control "sharing." There should be an area here to control the permissions or password for that folder. (This varies greatly depending on your version of Windows.)
Keep in mind that even with password protection turned on, if someone on your LAN has write access to your files, it is usually possible for them to infect your system with a virus. To try and prevent this from happening, we recommend only sharing specific folders instead of entire drives, and limit your sharing to folders that contain simple documents (and not executable program files).
For even more safety, strongly consider allowing "read-only" sharing. With this turned on, it would not be possible for a virus to infect your system using file sharing. You can control read-only settings in the same place as the password protection described above.
Beware Forged Emails & "Phishing" Scams
Do not implicitly trust any email you receive, especially ones from well-known companies that are likely to be targets of virus writers and scammers. These forged emails are a popular way of conning users into running viruses or giving away private information (called "phishing").
Most legitimate companies will never send you an executable attachment to run, and they will never ask you to submit private information via email (like credit card or bank account numbers) or through a form sent to you via email. Popular targets for these types of scams are software companies like Microsoft (fake software patches that are actually viruses), service companies like eBay and PayPal, financial institutions like banks and stock brokers, and other popular companies that deal with your private information.
If you receive an email from a company that contains an executable you did not request, delete it. (And consider updating your email software to disallow all executable attachments.)
If you receive an email from a company asking you to submit your private information either via email or via a web form sent to you via email, ignore it. If you suspect it may be legitimate, we recommend visiting the official website for that company by typing the URL by hand, and logging into your account with them as you normally would. Links provided to you in an email can be faked in many ways; they could obscure the actual URL you are viewing or use exploits to mask their real identity (a popular exploit in Internet Explorer). Typing the URL by hand insures you are going to the actual company website, e.g. www.microsoft.com, www.ebay.com, www.paypal.com, etc.
Here is an example of why these precautions are important. This screenshot is a very authentic-looking email received by one of our members in September 2003. It appears to come from Microsoft, warns of a security flaw, and provides an executable "patch" to fix the problem. In actuality it is a virus. There are many viruses in the wild today that are similar, and more to come.
A good website dedicated to informing people about phishing scams and exploits, and working to combat them, is the Anti-Phishing Working Group (APWG).
Practice Safe Computing
In addition to the safety measures discussed so far, you should follow these tips:
- Never open an attachment unless you are expecting it. Even then, only open attachments that you know are safe! This page on TechTV covers the long list of potentially dangerous file extensions (much more than just .exe). But with some clever techniques, some viruses can appear to be safe file types even when they're not! And since viruses now often forge information in their attack email messages, you might receive a virus which appears to come from a friend, but really doesn't. So to be safe, never open an attachment unless you are expecting it, and it has been scanned for viruses.
- Only download programs from trusted sources, and even then, be sure to use your A/V software to check your downloads for viruses.
- Scan all floppy disks and CD-ROM's for viruses before using them. Be extra careful with floppy disks and CD-ROM's that come from outside sources, such as your kid's school, your spouse's office, or any place with access to many people -- these are virus havens.
- Don't forget to update your internet programs after re-installing
a program from scratch. Often, you will find the need to re-install
Windows or a program, from scratch. When this happens, it is important
to remember to download the latest patches and apply them to all
changed programs. Too often we have heard of people installing Windows
from scratch, and they forget to download the latest version of
Internet Explorer. Next thing you know, they're infected with a
virus that exploits known bugs in earlier versions of MSIE.
Conclusion
Keeping your computer safe from viruses and hackers can be summed up quite simply:
- Keep the Internet separated from your computer network as much as possible.
- Prevent other computers from having access to your files as much as possible.
- Keep your operating system and programs up-to-date with security patches and upgrades.
- Don't implicitly trust anything you receive from the Internet (no matter who it comes from).
- Always virus-scan all files that come from the Internet or other sources.
For More Information
- Microsoft's Three Steps to Help Ensure Your PC is Protected
- Microsoft's Security for IT
- Microsoft's Security Bulletin Search
- Microsoft's Free Virus-Related Phone Support for U.S. and Canada: 1-866-PCSAFETY
- Symantec's Security Response Anti-Virus Site and Advisories
- Symantec's Security Check page, to see if you're vulnerable to known attacks
We hope this document has helped you. For computing help and advice from your peers, please use the iATN PC Users Forum. If you have any questions or concerns about this document, please contact iATN Support.